Table of contents
No headings in the article.
In today's competitive job market, having a strong understanding of Azure networking concepts can set you apart from other candidates. Whether you're preparing for an interview or looking to deepen your knowledge, this article will provide you with essential Azure networking interview questions and answers. From virtual networks to load balancing, we'll cover the key topics that you need to know to excel in your next interview. Let's dive in and explore the critical aspects of Azure networking that every aspiring cloud professional should master.
Let's start.
Question 1 :
What is the difference between NSG and ASG?
ASGs are applied to VMS and are used in conjunction with NSGs. By associating an ASG tag with a network security rule, you can define rules that apply to a group of VMS sharing the same tag.
ASGs simplify the management of security rules in a multi-tier application by grouping VMS that belong to the same application tier. This makes it easier to apply and manage security policies for a specific application.
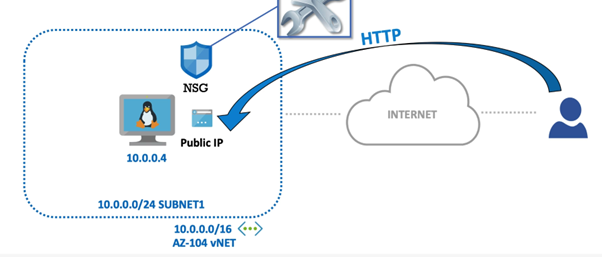
How can you block the access to a your vm from a subnet ?
By default traffic is allowed between subnets with in the VNet in Azure. This is because of a default NSG rule "AllowVnetlnBound".
The priority of this rule is 65000, so we need to create a Deny rule with less than 65000 priority number.
Are Azure NSGs stateful or stateless ?
They are stateful in nature. That means if you allow a port for inbound traffic traffic to receive the request. You don't have to open the port in outbound rules to send response back.
Example: If you host a host an application on port 80 in azure vm and allow inbound traffic for customers to access it. You don't need to open port 80 in outbound traffic to send response back to the customer.
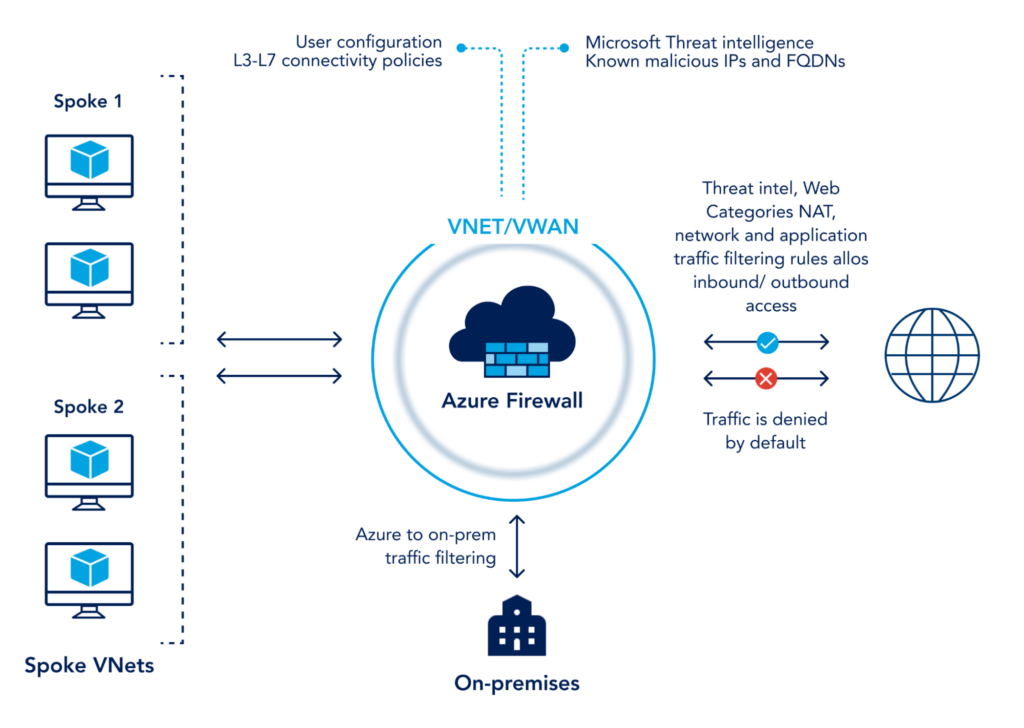
What is the difference between Azure Firewall and NSG ?
FireWaII: Designed for controlling both outbound and inbound traffic to and from resources within a Virtual Network (VNet).
NSC: Typically associated with subnets or individual network interfaces to control traffic within a VNet and between VNets.
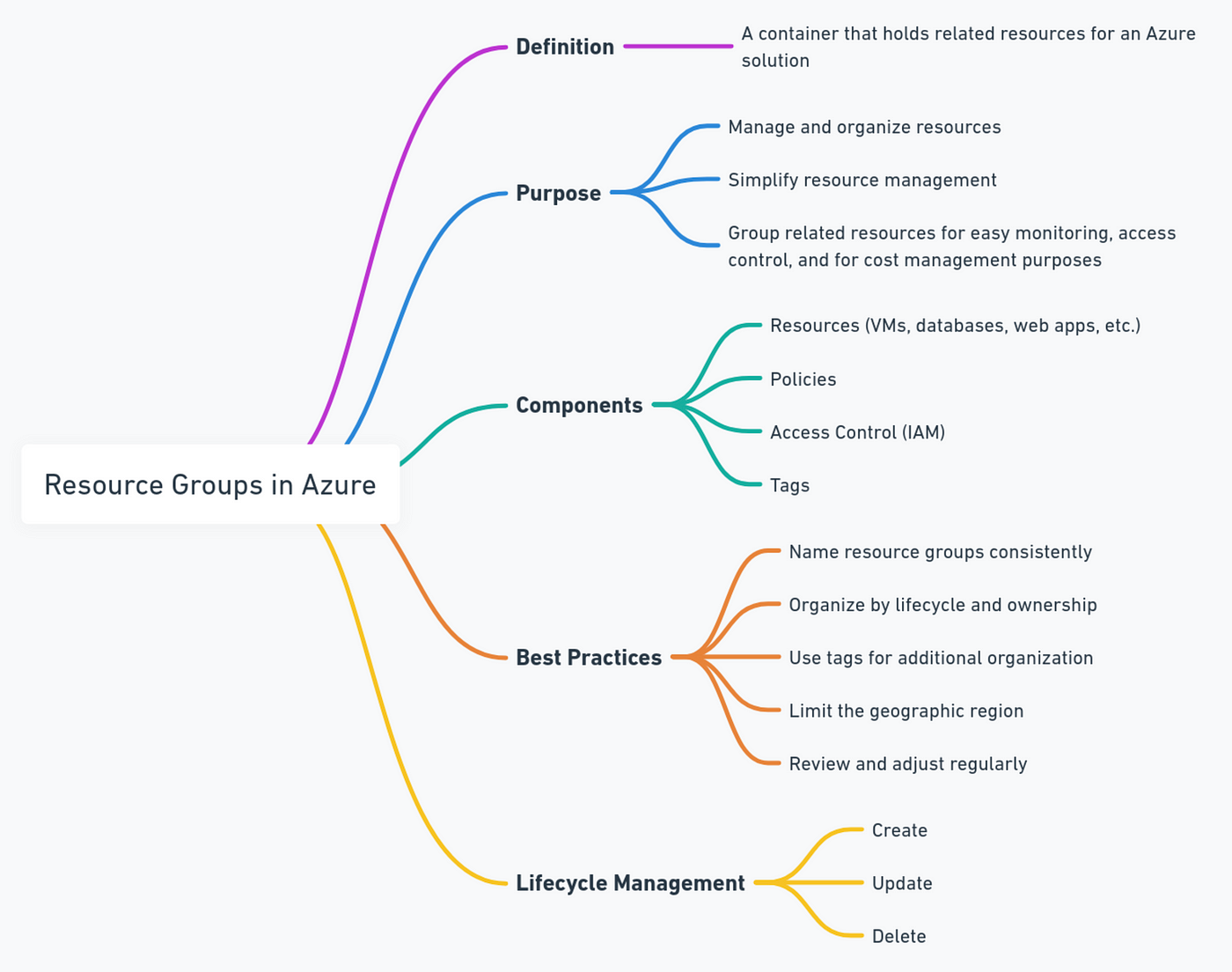
What are the advantages of resource groups in azure ?
Organizational Structure: They enable logical grouping of related resources, simplifying management and organization.
Management and Automation: Bulk operations, such as updates or deletions, can be performed on all resources within a group. Azure Resource Manager (ARM) templates facilitate automation of deployment and configuration.
Access Control and Security: Role-Based Access Control (RBAC) allows setting and managing permissions at the Resource Group level, enhancing security.
Cost Management and Budgeting: Resource Groups help track and manage costs, aiding in budget control and financial oversight.
Resource Lifecycle Management: Deploy, update, and delete all resources within a group together, simplifying lifecycle management.
Compliance and Governance: Apply Azure Policies at the Resource Group level to enforce compliance with organizational standards and regulatory requirements.
Tagging and Organization: Tags allow categorization and organization of resources for better management and reporting.
Resource Dependencies: Efficiently manage dependencies and relationships between resources within the same group.
Monitoring and Insights: Centralized monitoring provides access to metrics and logs for all resources in a group from a single location.
Consistency: ARM templates and Azure Blueprints ensure consistent and repeatable deployments.
These advantages streamline resource management, improve security, and enhance operational efficiency in Azure.
What is the difference between Azure User Data and Custom Data ?
User data is a new version of custom data and it offers added benefits. User data persists and lives in the cloud, accessible and updatable anytime. Custom data vanishes after first boot, accessible only during VM creation.
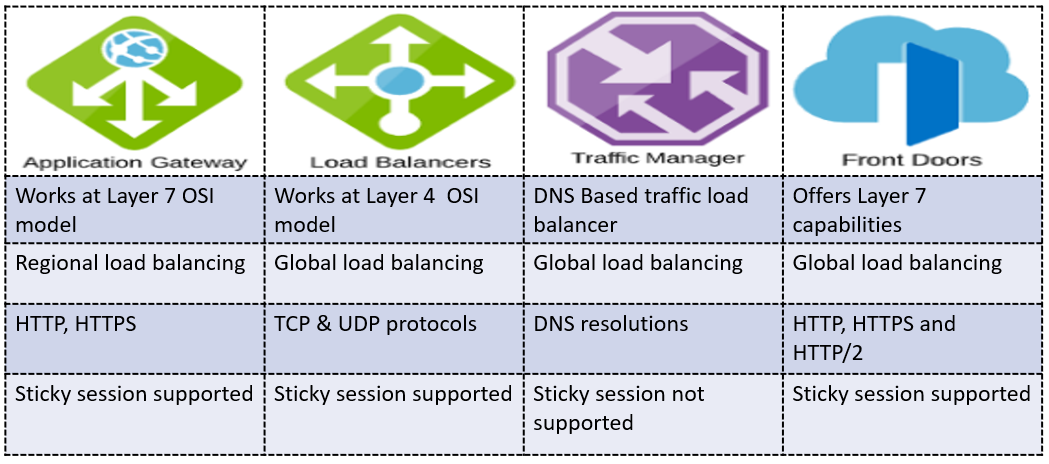
What is the difference between Azure App Gateway and Azure Load Balancer?
Azure Application Gateway: Operates at Layer 7 (Application layer) of the OSI model. Provides advanced application-level routing, SSL termination, and web application firewall (WAF) capabilities. Suited for distributing traffic based on application awareness.
Azure Load Balancer: Operates at Layer 4 (Transport layer) of the OSI model. Distributes network traffic based on IP address and port. Suitable for generic TCP/UDP load balancing without application-specific features.
Assume your company is using all the ideal Azure Networking setup and your application is deployed in the web subnet , Explain the traffic flow to your app?
User Request: A user sends a request to access your application from their device (e.g., browser or mobile app).
DNS Resolution: The user's device performs a DNS lookup to resolve your application's domain name to an IP address. Azure DNS (or another DNS service) responds with the IP address of your application's load balancer.
Load Balancer: The request is routed to the Azure Load Balancer (ALB), which distributes incoming traffic across multiple instances of your application for scalability and high availability.
Network Security Group (NSG): The ALB is associated with an NSG that filters incoming traffic based on configured security rules. The NSG allows or denies traffic based on source IP addresses, ports, and protocols.
Web Subnet: The filtered traffic is routed to the web subnet where your application instances are deployed.
Application Instance: The request is received by one of the application instances, which processes the request and generates a response.
Web Subnet: The response is sent back to the web subnet.
Network Security Group (NSG): The response traffic is filtered again by the NSG to ensure security and compliance.
Load Balancer: The response is routed back to the ALB, which directs it to the user's device.
User Device: The user receives the response from your application, completing the request.
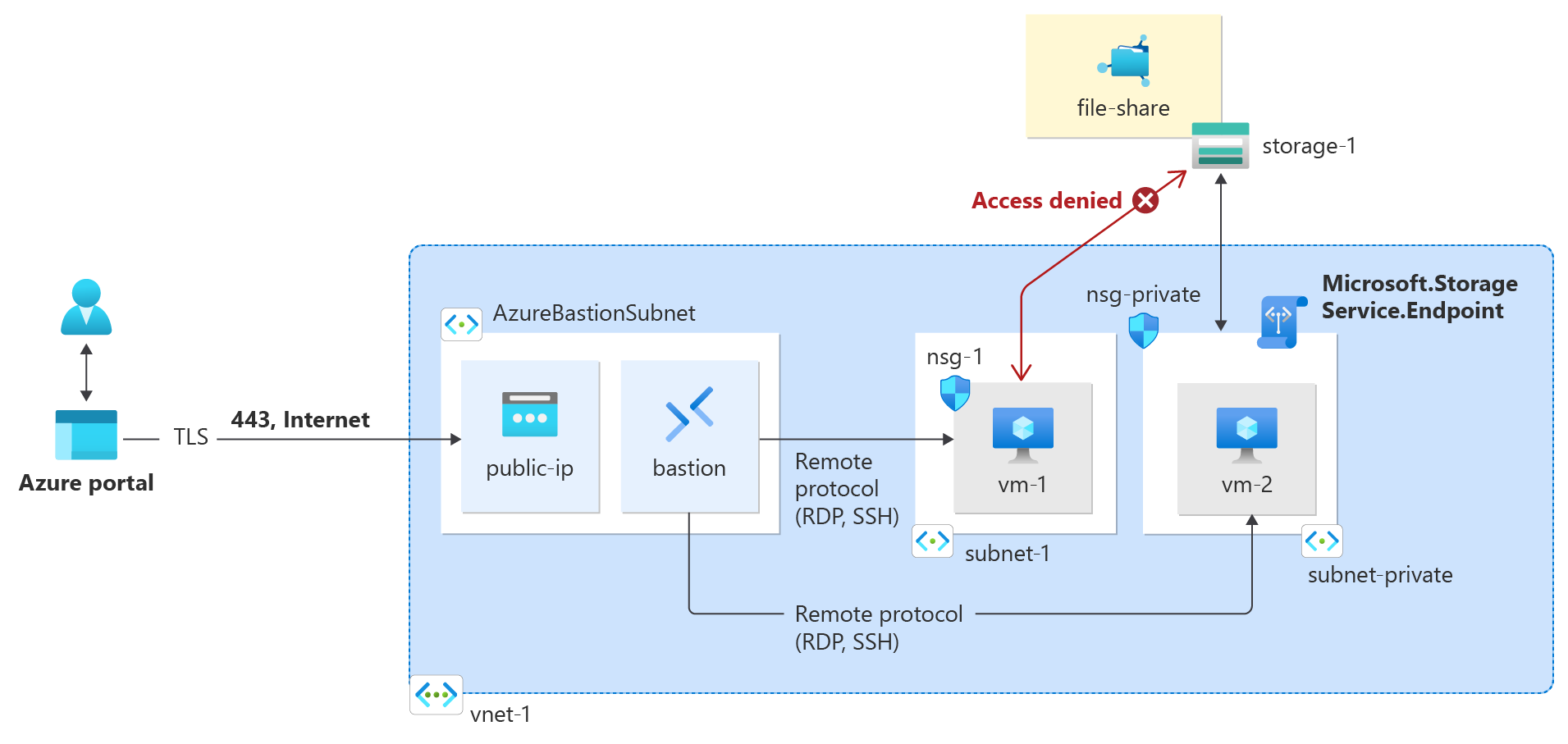
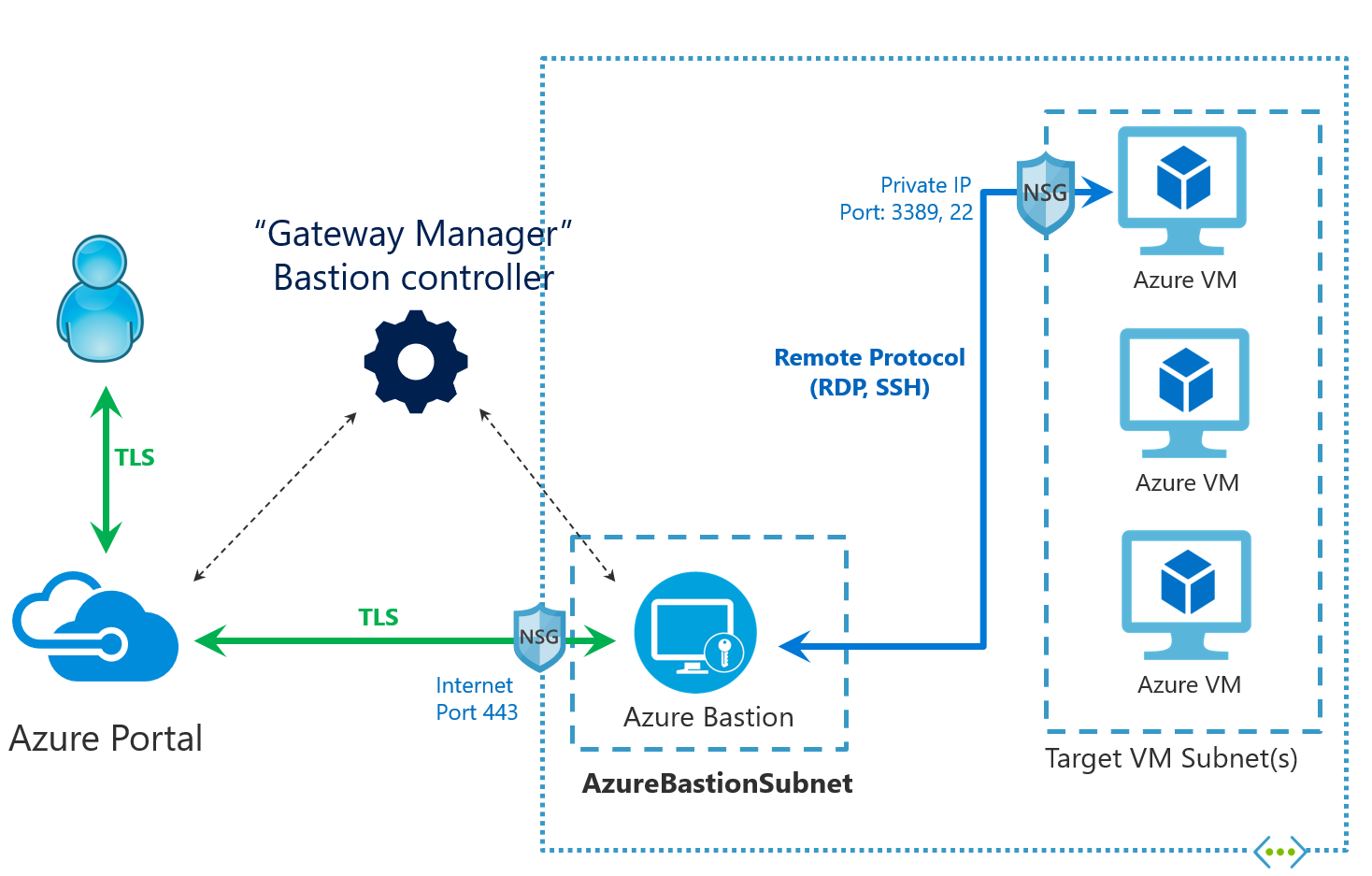
Describe the purpose of Azure Bastion and when it is used for secure remote access to virtual machines?
Secure Remote Access
Elimination of Public Internet Exposure
Reduced Attack Surface
Azure Bastion Integration
Simplified Connectivity
Azure Portal-Based Access
Role-Based Access Control (RBAC)
Multi-Factor Authentication (MFA)
Audit and Monitoring
In conclusion, mastering Azure networking concepts is crucial for any cloud professional aiming to excel in their career. Understanding the differences between NSGs and ASGs, the stateful nature of Azure NSGs, and the distinctions between Azure Firewall and NSGs are fundamental. Additionally, knowing the advantages of resource groups, the differences between Azure User Data and Custom Data, and the functionalities of Azure App Gateway and Azure Load Balancer can significantly enhance your expertise. By familiarizing yourself with these key topics, you will be well-prepared for your next interview and equipped to manage Azure networking effectively in real-world scenarios.
